OAuth 2.0 Implementation Using Mule OAUTH2 Provider

Introduction
Transform your Mule 4 applications into fortresses of data security with the captivating power of OAuth 2.0 Implementation using Mule OAuth 2.0 Provider. Unleash seamless authentication and authorization, enabling a dance of secure access tokens across your API endpoints. Mule's dynamic capabilities make configuring OAuth 2.0 flows a breeze, ensuring a spellbinding balance of accessibility and protection.
Mule OAuth 2.0 provider module
The Mule OAuth 2.0 Provider module, available on Anypoint Exchange, transforms a Mule Application into an OAuth provider, playing a key role in the OAuth 2.0 dance. This module enables the application to authenticate clients, issue tokens, validate tokens and manage client registrations or deletions within a flow. With four essential operations,
1. CREATE CLIENT
2. DELETE CLIENT
3. VALIDATE TOKEN
4. REVOKE TOKEN
This module provides a comprehensive toolkit for building secure, OAuth 2.0-compliant authentication and authorization processes seamlessly into Mule applications.
Prerequisites
- Create a Mule project in Anypoint studio and name it as you like.
- Search and add Oauth 2.0 provider module from Anypoint Exchange.
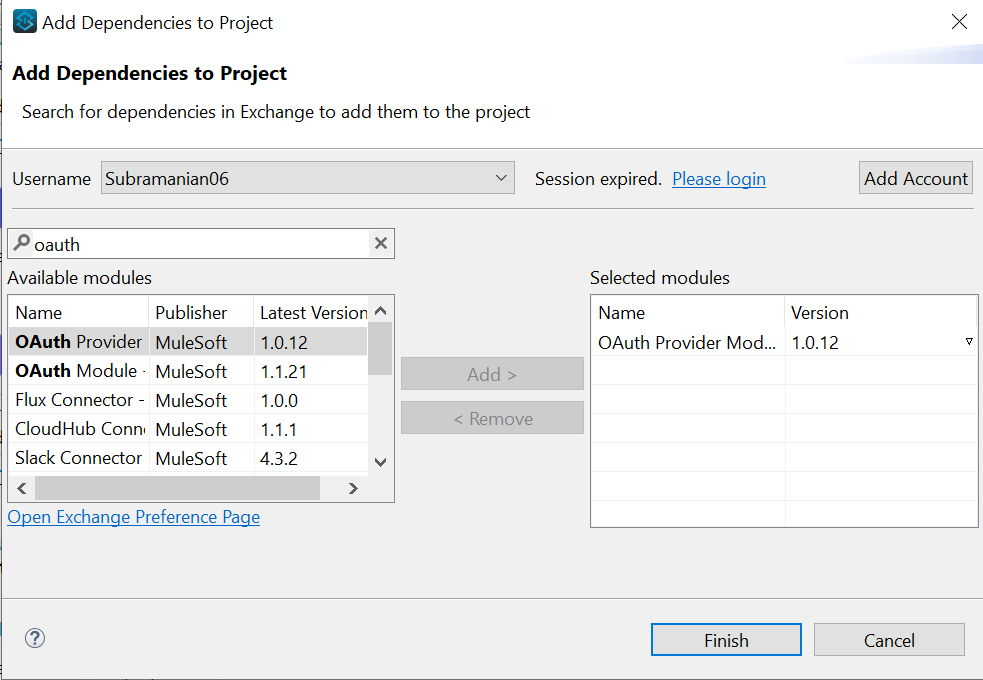
Implement Mule OAUTH 2.0 Provider
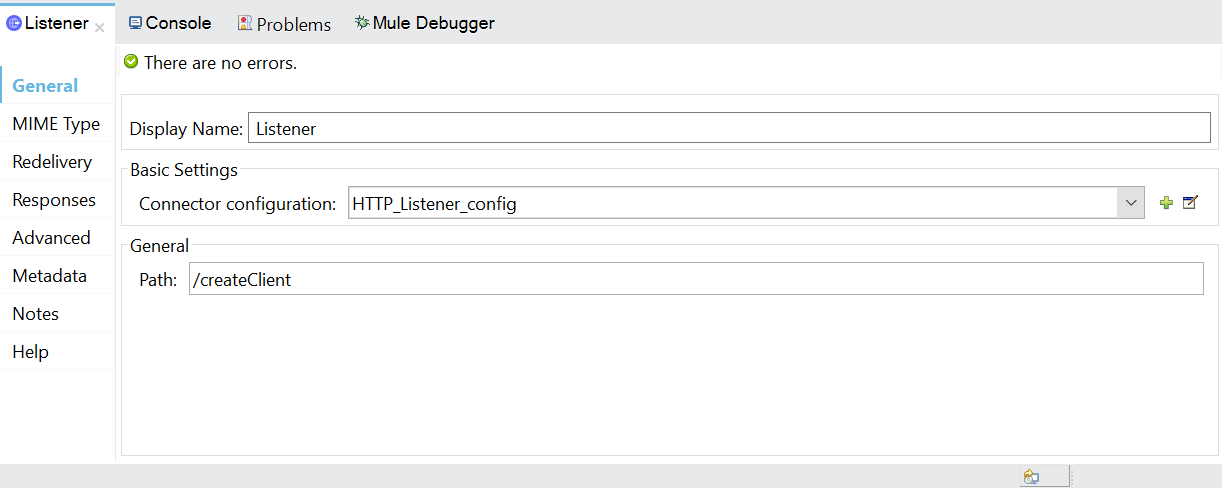
- Now drag HTTP Listener component from mule palette.
- Configure HTTP Listener Global configuration with default values and set path as /createClient.
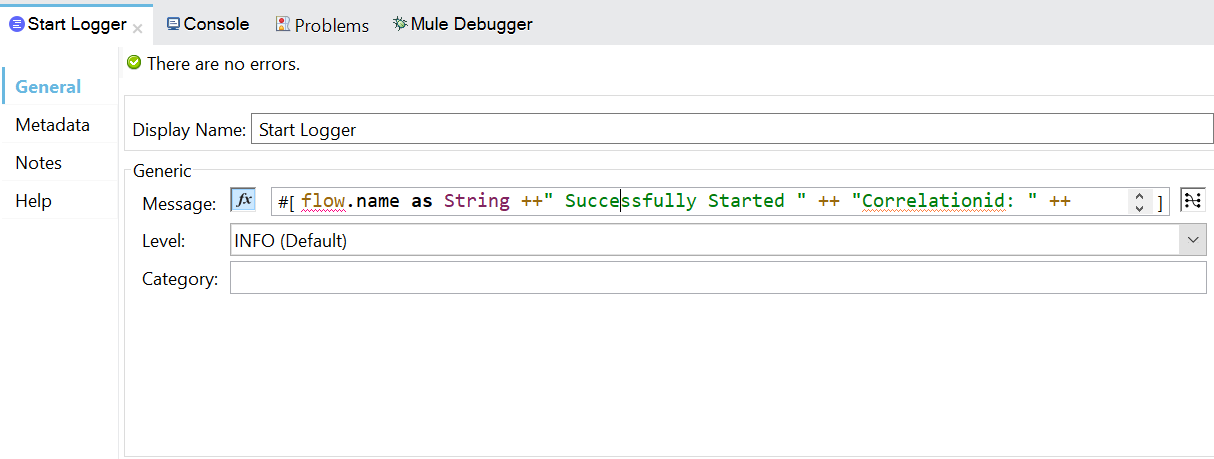
- You can place a logger at the beginning of the flow.
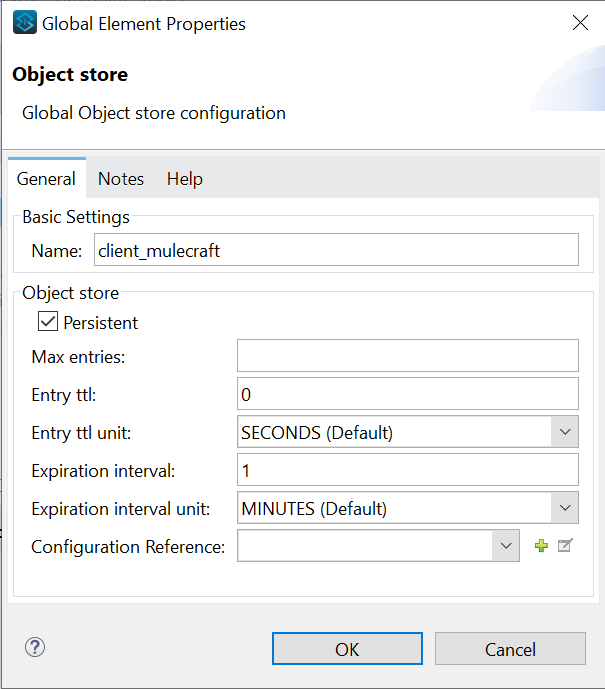
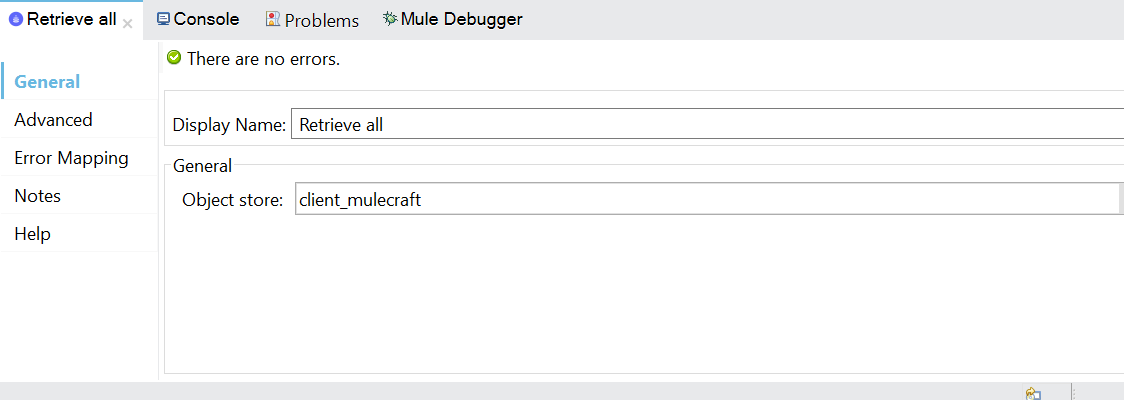
- Create two object stores in which ‘client credentials’ and ‘tokens’ are stored.
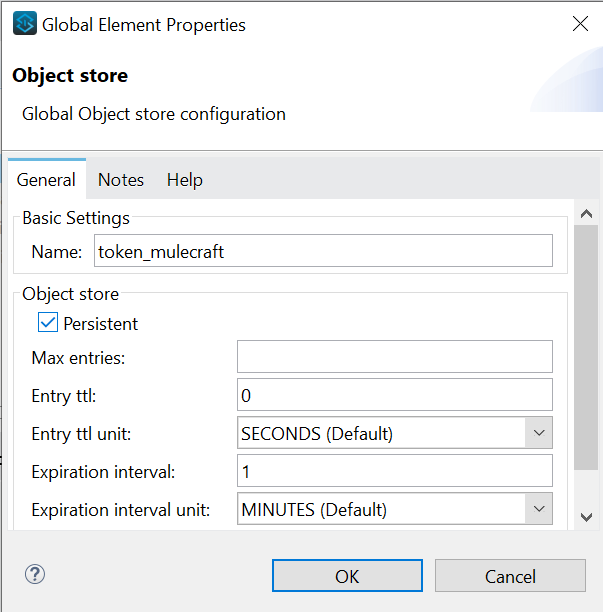
- Mule 4 allows easy interaction with object storage services, enabling efficient storage and retrieval of data. With streamlined payload transformation, robust exception handling, secure credential management and enhanced logging capabilities, Mule 4 ensures smooth integration workflows. It supports features like versioning, metadata handling and batch processing for optimal data management. Mule 4's advanced capabilities make it a powerful tool for developers orchestrating interactions with object stores in modern integration scenarios.
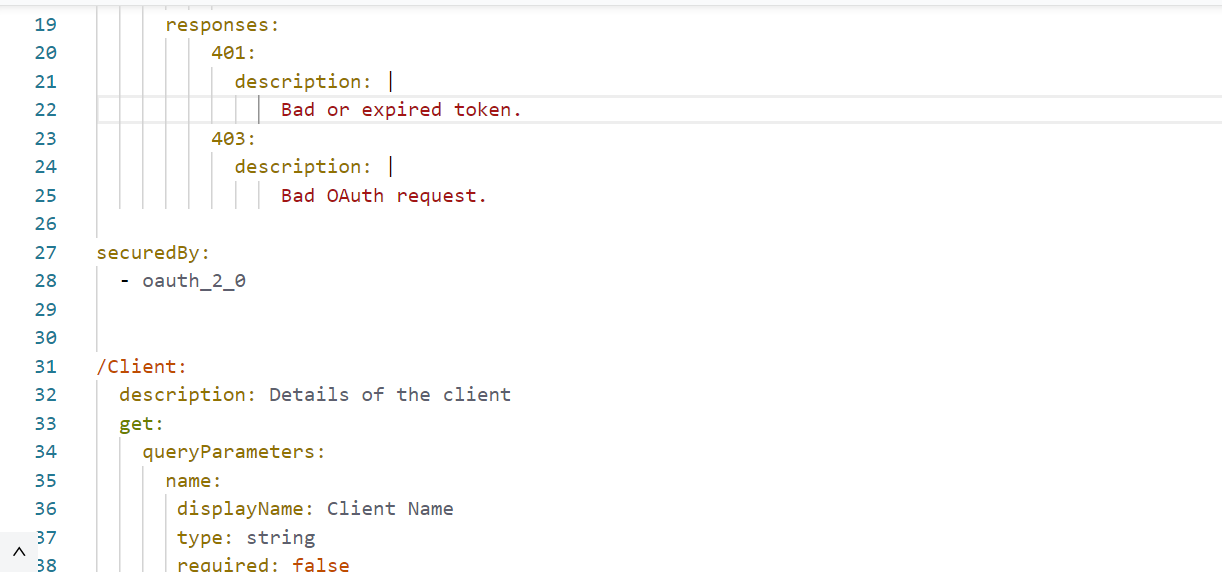
- Listener config: HTTP listener configuration through which Mule OAuth 2.0 provider is listening.
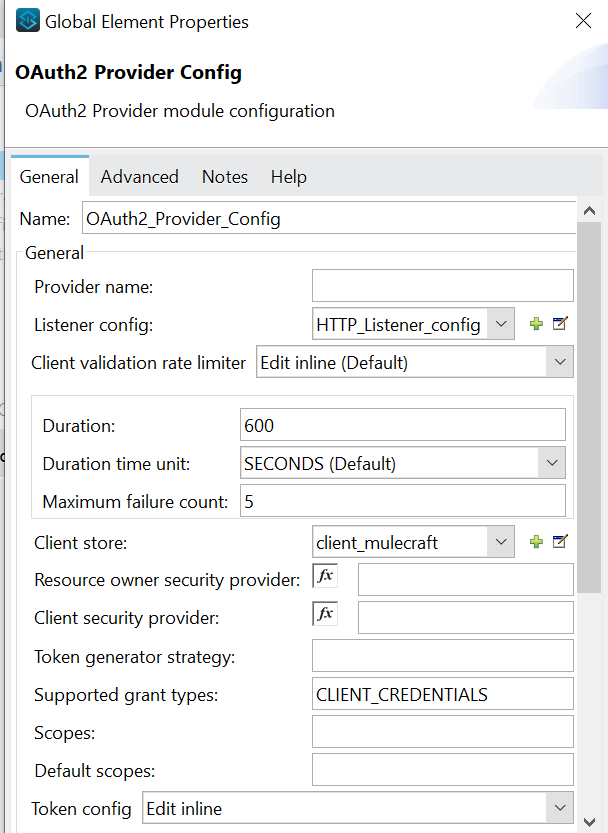
- The Mule OAuth client store caches each valid client application(client credentials) for which a token is requested.
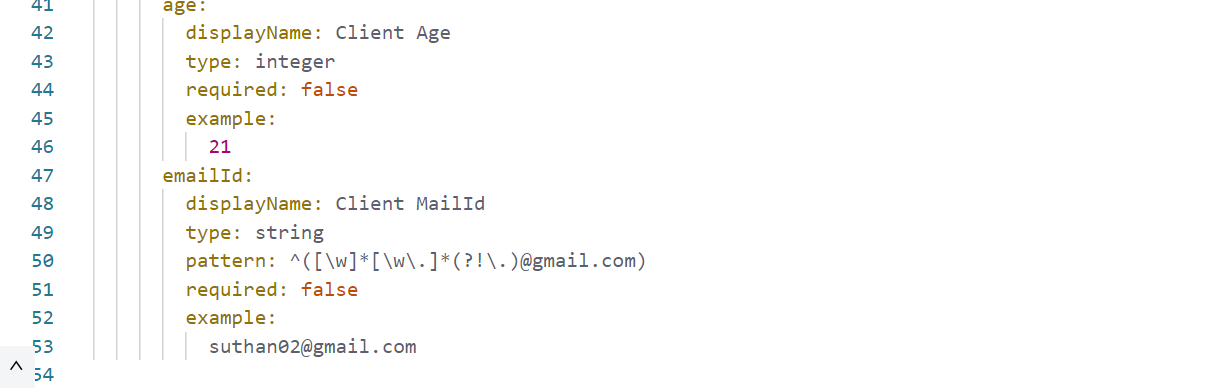
- Pass the supported grant types as CLIENT_CREDENTIALS, path as /token to get the token and configure the token object store to store the token value, you can configure the token TTL as per requirement, I have kept is as default value and refresh token strategy as No Refresh Token as Default value
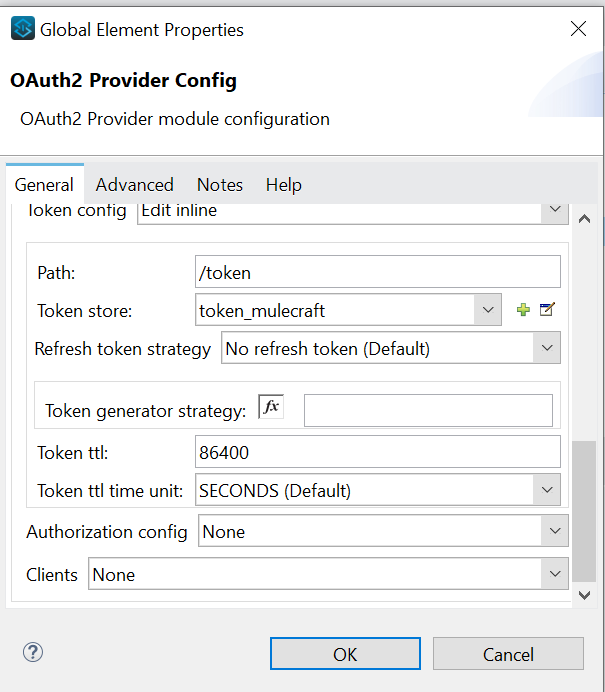
- Select the OAuth2 provider config created in module configuration tab.
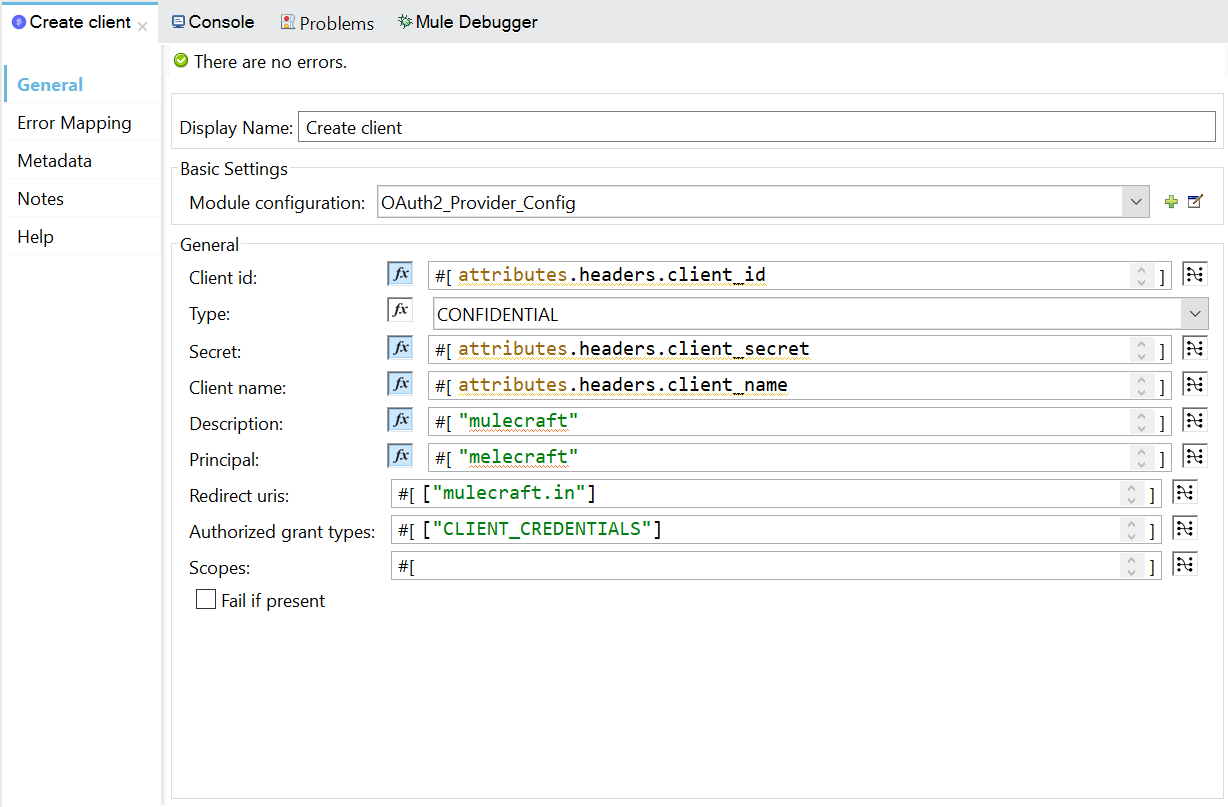
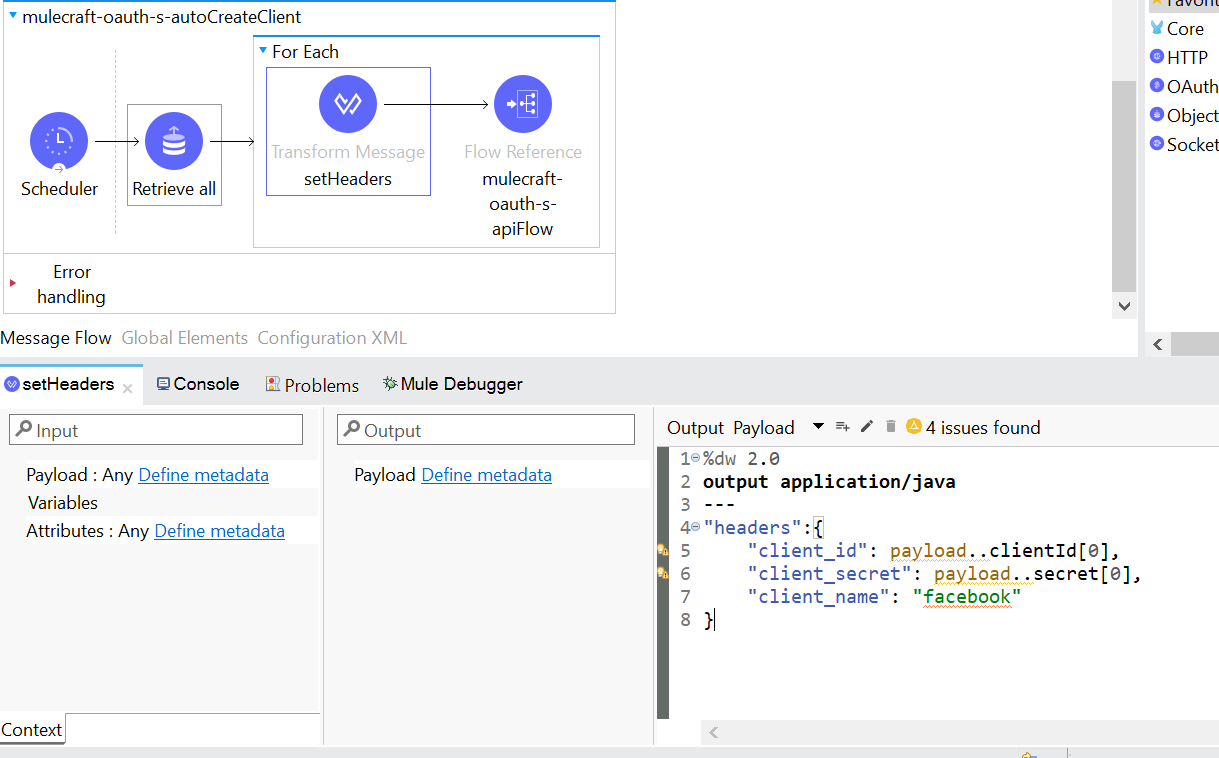
- Client id, client secret, client name are passed from client as headers.
- Description, principal and redirect URIs are hard coded. You can pass these values from client or hard code depends on requirement.
- CLIENT_CREDENTIALS are used as Grant type.
- No scopes are declared.
- Type is selected as Confidential to maintain confidentiality of the credentials.
- If Fail if present is ticked, it doesn’t allow to create duplicate clients.
- Add a set payload component and set the value to “Client created successfully
CREATE CLIENT
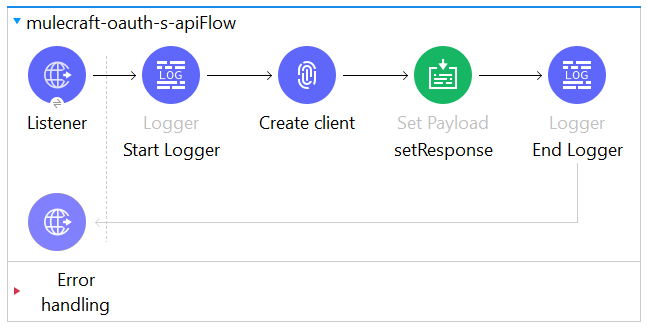
VALIDATE TOKEN
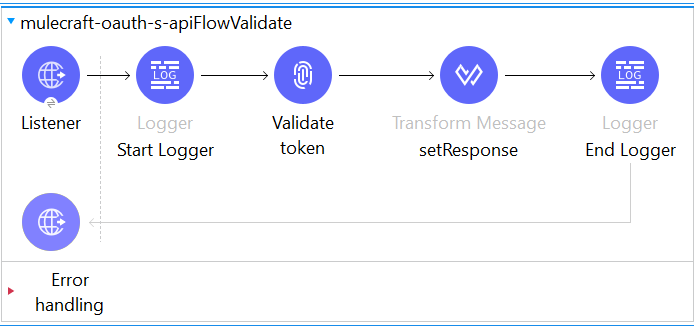
Create a flow and add HTTP listener with path /validate.
- Add an HTTP listener config.
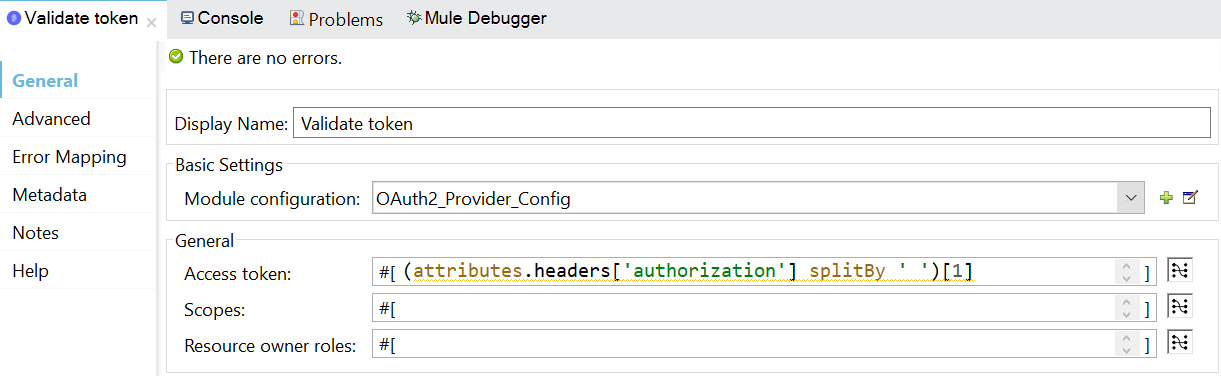
- Add Validate token operation and fill the required fields.
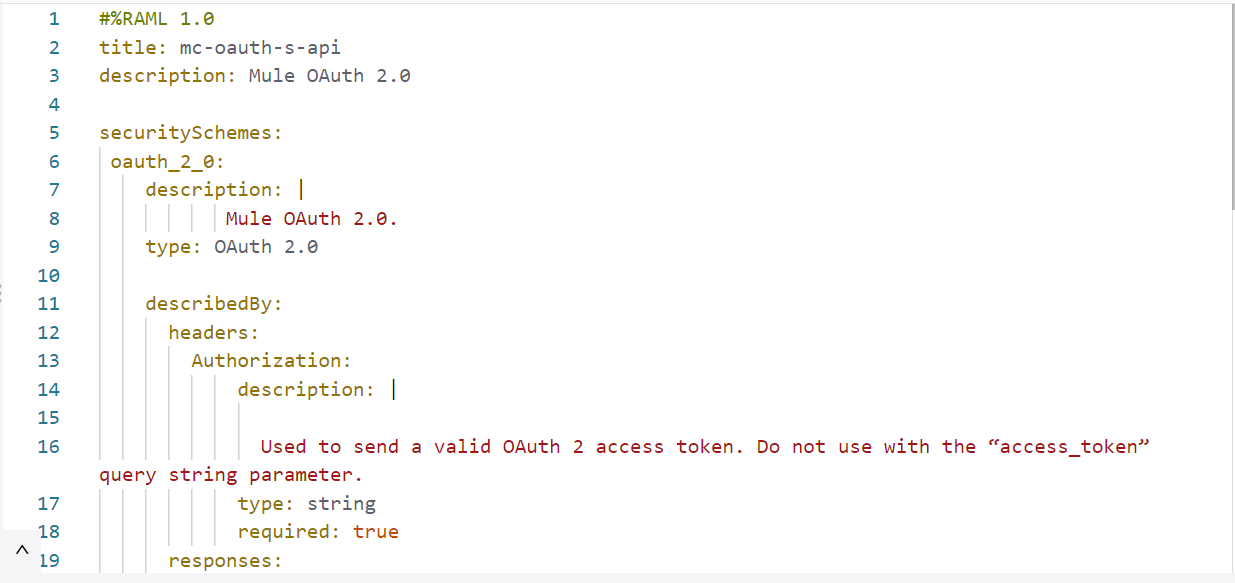
Add OAuth 2.0 in raml
- Modify the RAML of the mule application.
- Publish the modified RAML to exchange.
- Deploy your application in runtime manager.
- Add your application in API manager.
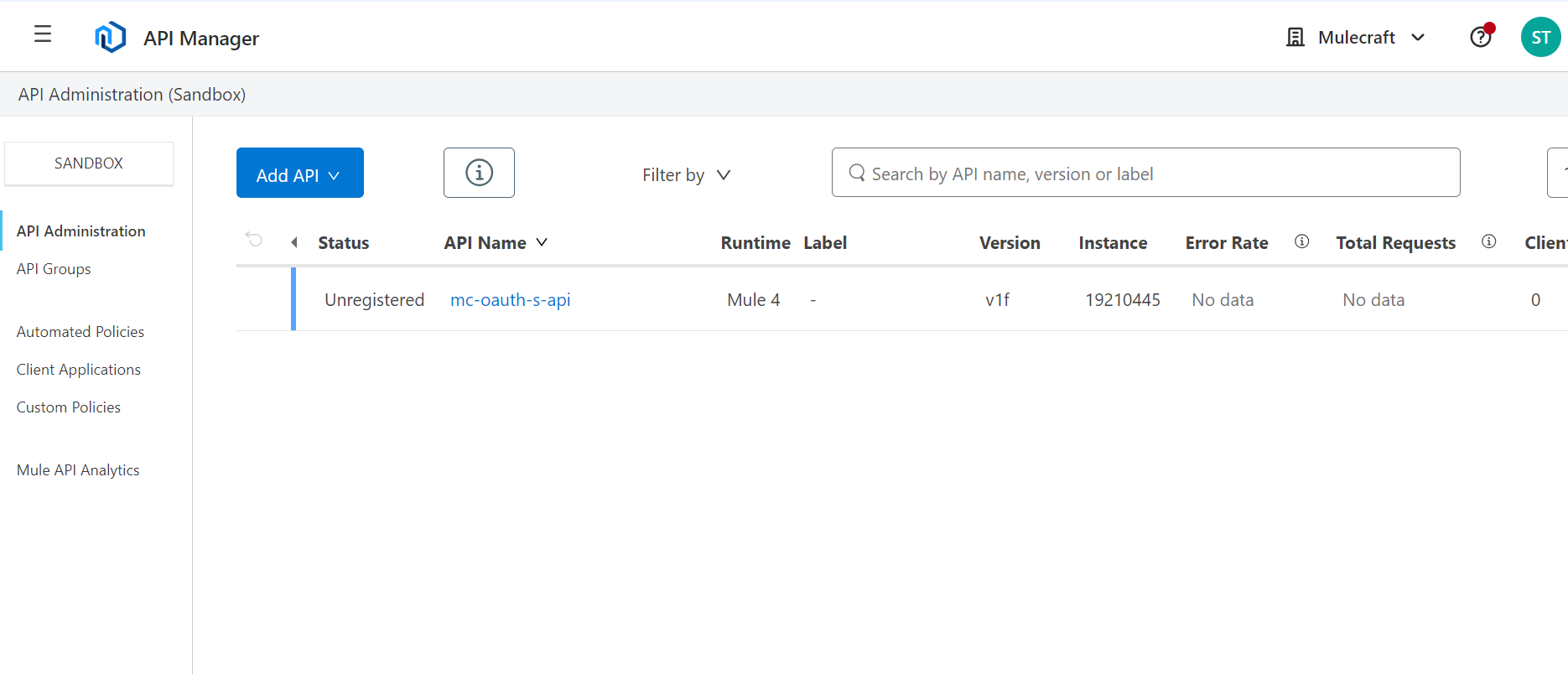
- Add client_id and client_secret to properties in runtime manager from api manager.
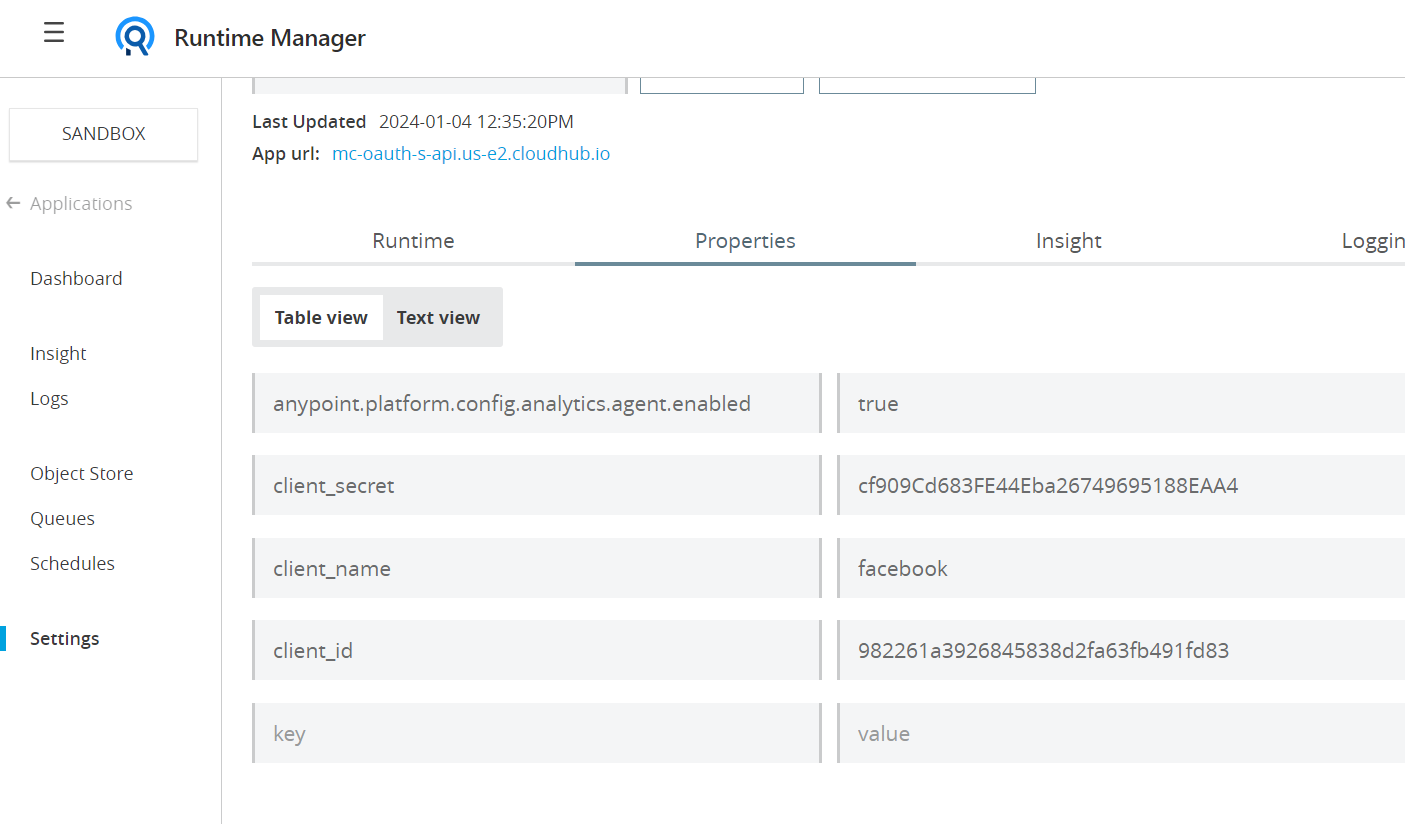
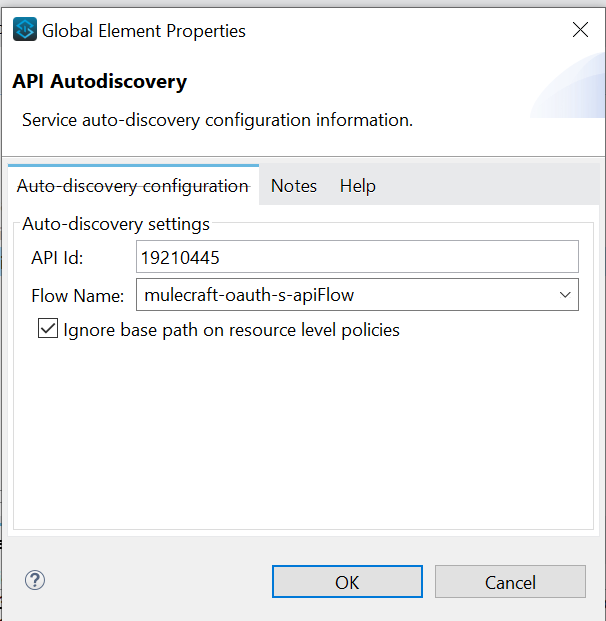
- Add instance id from api manager to API auto discovery configuration in Anypoint studio.
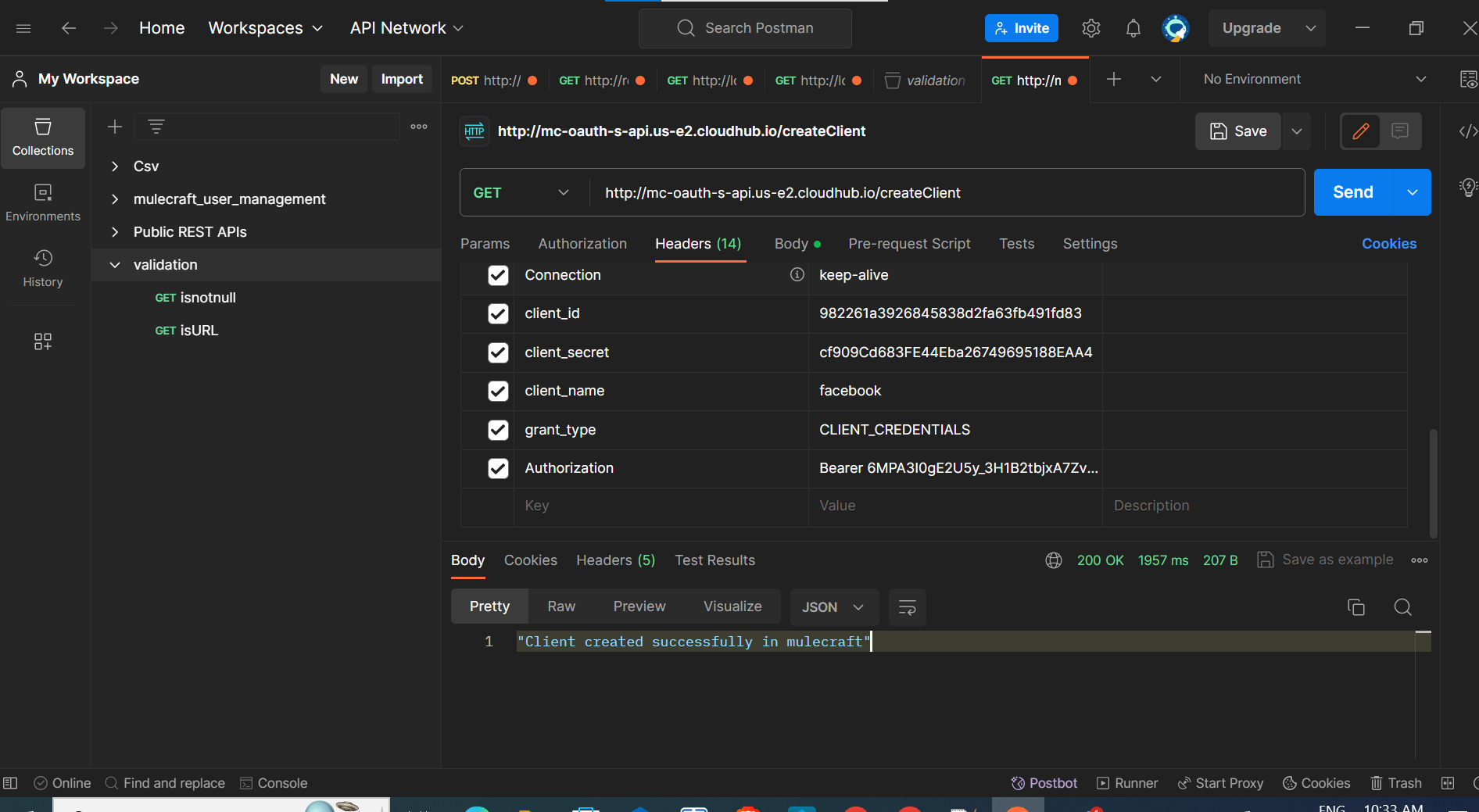
- Lets test from POSTMAN.
- Provide the client_id and client_secret generated.
- Provide Grant Type as CLIENT_CREDENTIALS.
- Provide the access token as Bearer token in Authorization field.
- Set createClient as endpoint to successfully create a client.
- Client credentials in object _clientStore last only for 30 days.
- Instead of adding client credentials every time after 30 days, we can achieve auto refreshing of client credentials by creating a flow with Scheduler.
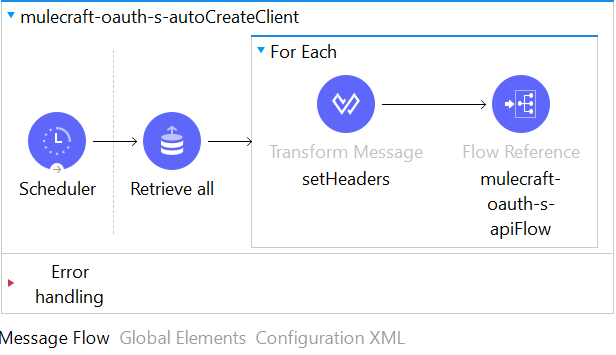
- Set the scheduler frequency to 20 days (or any number less than 30).
- Retrieve all the the client_id’s from object _clientStore.
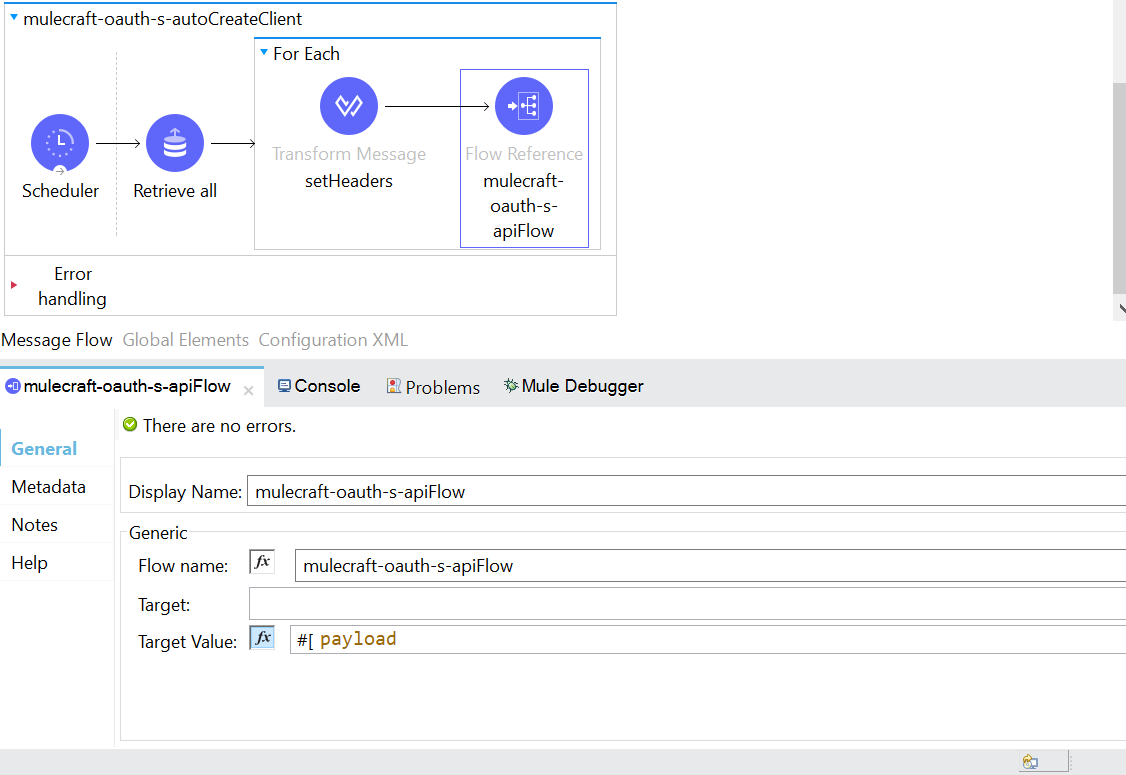
- Send each client id to create client flow using For Each.
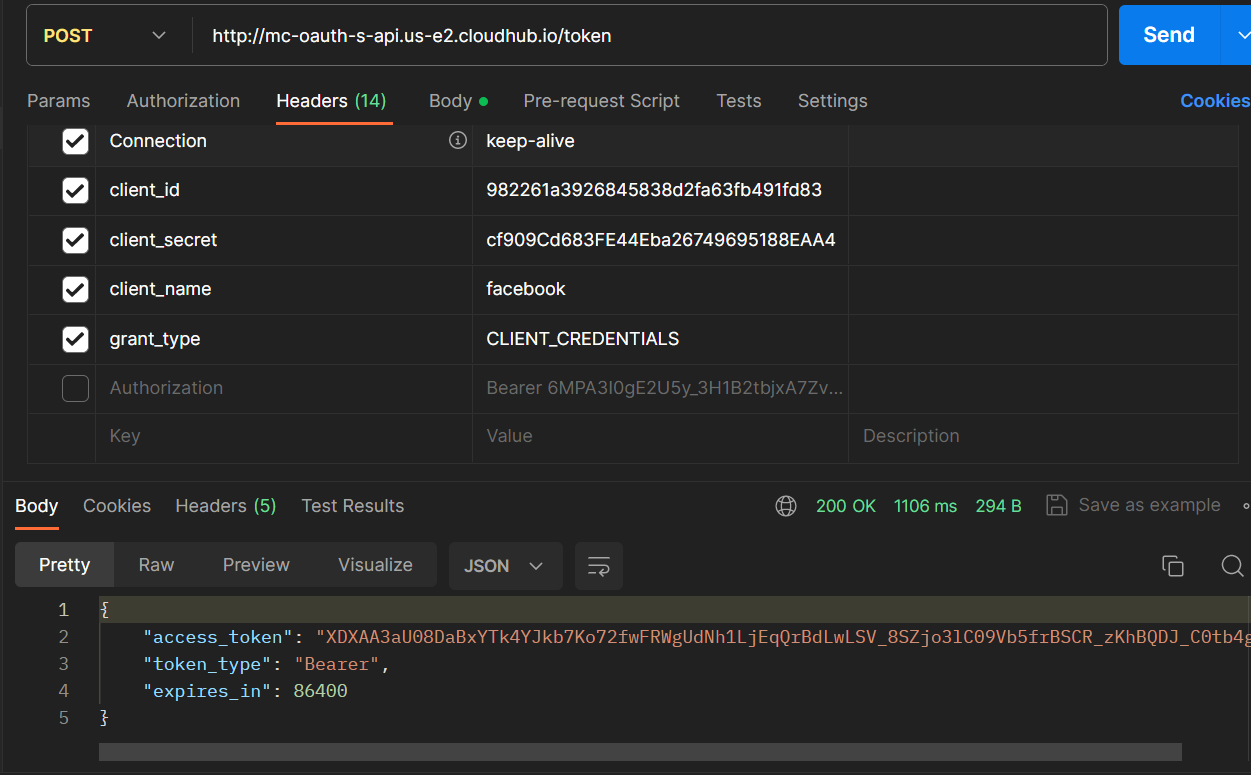
Get Access Token
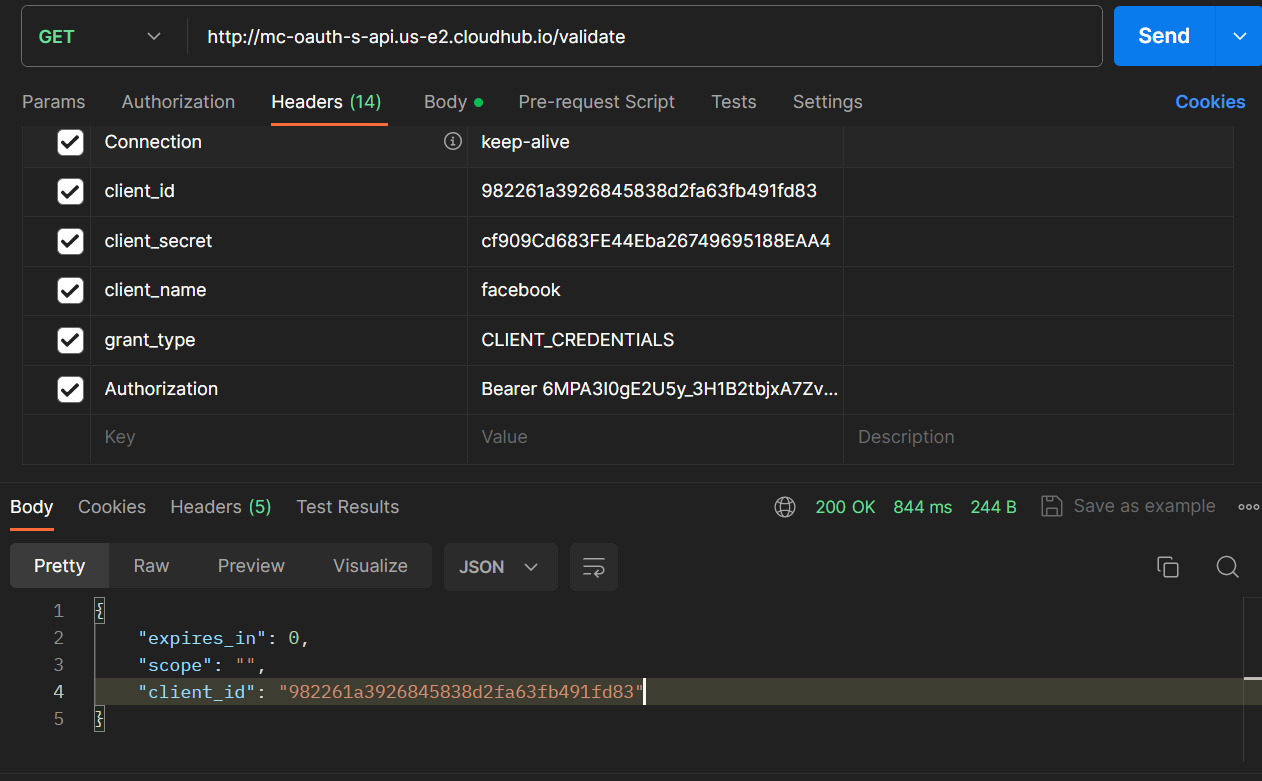
- Set validate as endpoint to validate the token.
Conclusion
In conclusion, implementing an OAuth 2.0 provider for a blog ensures secure user authentication and controlled access. OAuth 2.0's standardized protocol enhances the security by using access tokens, reducing risks associated with unauthorized access. The user-friendly authorization process and consent mechanisms foster transparency, granting readers control over shared information. Its adaptability supports seamless integration with third-party applications, while token management features contribute to a robust security posture.
Elevate your Mule 4 projects with an enchanting layer of standardized, fortified security, where data protection becomes a magical journey guided by OAuth 2.0 protocols.